Menu
Bounties /Pin to ProfileBookmark
Is this login process safe enough?
Login process can be done in many ways. Searching for a solution, I found that there was some consensus about the principles, but no consensus on how to implement them. Hence I did it “my way” by isolate all sensitive parts from the internet.
My question is if I am thinking in the wrong direction or if there is something I missed? (Except for the hashing and salting that will be implemented in production)
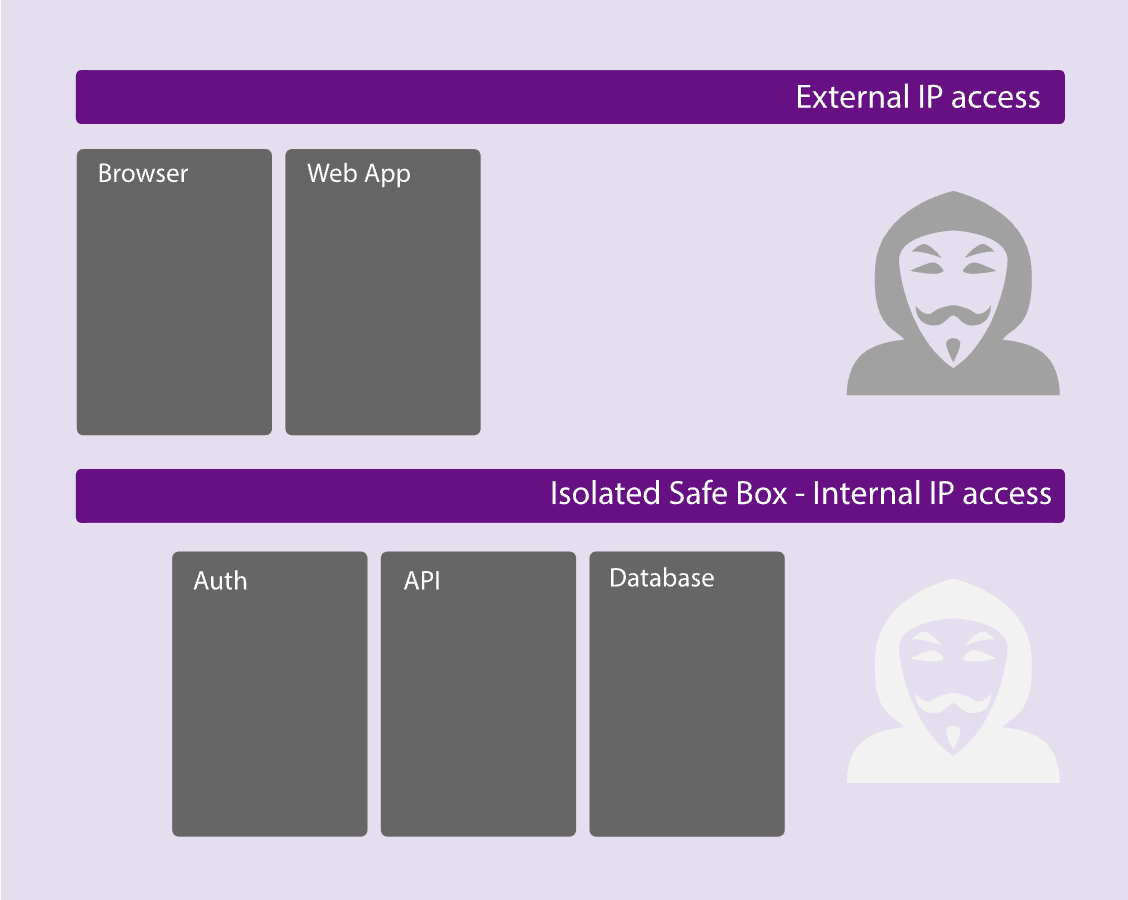
Detailed description here and live version here . Mail [email protected] and password: password
Sign in
to post a answer @neststayhome
@neststayhome